In today’s digital landscape, safeguarding your business from cyber threats is more critical than ever. The Essential Eight Cybersecurity framework, developed by the Australian Cyber Security Centre (ACSC), provides a robust set of strategies designed to help organisations enhance their cybersecurity posture. In this guide, we will look into each of the Essential Eight strategies, their benefits, and practical steps for implementation, ensuring your business stays protected against evolving cyber threats.
Introduction to Essential Eight Cybersecurity
The Essential Eight is a set of baseline mitigation strategies recommended by the ACSC to protect systems against a range of cyber threats. Implementing these measures can significantly reduce the risk of cyber incidents and improve overall security resilience.
Detailed Breakdown of Each Essential Eight Strategy
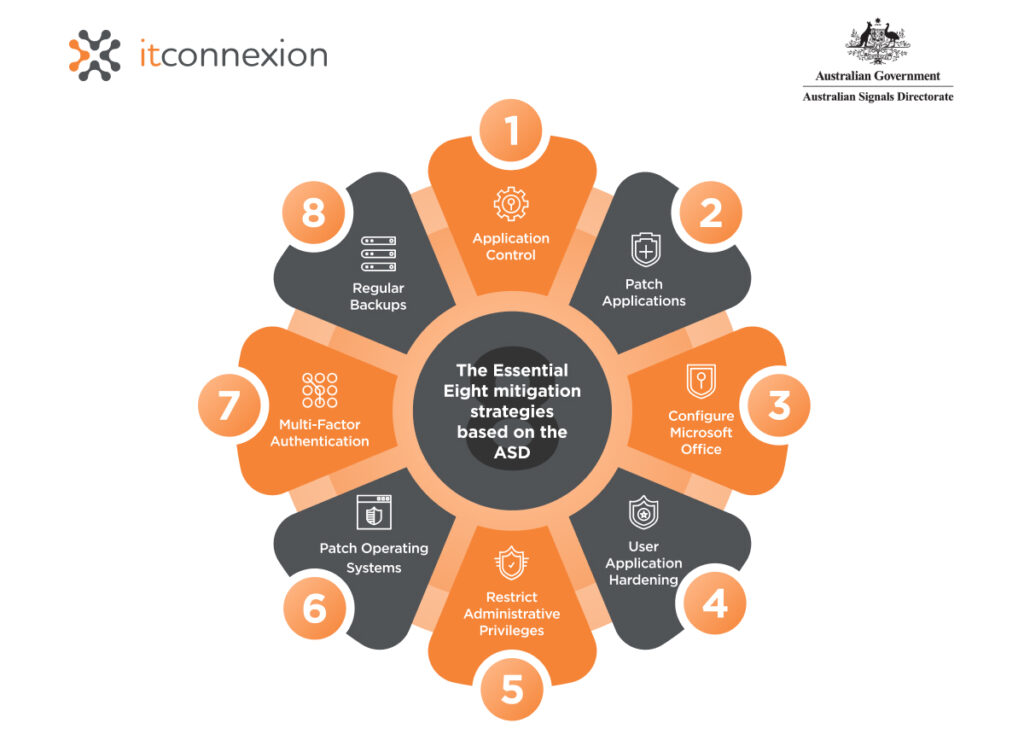
- Application Control
Application control helps prevent malicious software and unapproved applications from executing. By restricting the applications that can run on your systems, you minimise the risk of malware infections.
- Patch Applications
Regularly patching applications ensures that security vulnerabilities are addressed promptly. This prevents cybercriminals from exploiting known flaws to gain unauthorised access to your systems.
- Configure Microsoft Office
Macro Settings Configuring macro settings to block macros from the internet and only allowing vetted macros reduces the risk of macro-based malware attacks.
- User Application Hardening
Hardening user applications by disabling unnecessary features and functionality, such as Adobe Flash and Java, reduces the attack surface and limits the opportunities for exploitation.
- Restrict Administrative Privileges
Limiting administrative privileges to essential personnel and regularly reviewing and reassessing these privileges prevents unauthorised access and reduces the impact of potential breaches.
- Patch Operating Systems
Just like applications, operating systems require regular updates to fix security vulnerabilities. Ensuring timely patching of OSs is crucial for maintaining system integrity.
- Multi-Factor Authentication
Implementing multi-factor authentication (MFA) adds an additional layer of security, making it more difficult for attackers to gain access even if they obtain user credentials.
- Regular Backups
Regularly backing up important data and verifying the integrity of these backups ensures that you can recover quickly in the event of a ransomware attack or data loss incident.
Benefits of Implementing Essential Eight Cybersecurity Measures
- Enhanced Protection Against Cyber Threats:
By addressing common vulnerabilities and implementing multiple layers of defense, the Essential Eight significantly reduces the risk of cyber attacks.
- Improved Compliance with Industry Standards: Many regulatory frameworks and industry standards recommend or require the implementation of these cybersecurity measures.
- Reduced Risk of Data Breaches and Cyber Attacks:
Proactively addressing potential security weaknesses helps prevent data breaches and minimises the impact of any incidents that do occur.
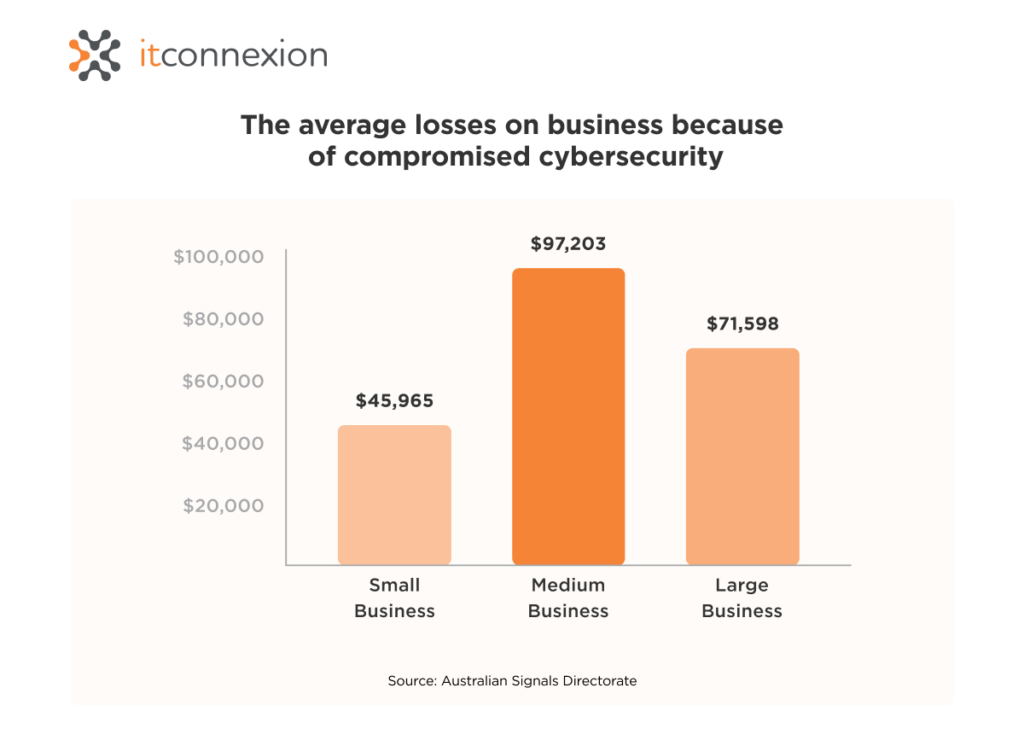
Take a look at the average loss of Australian business because of weak cybersecurity:
Practical Steps for Implementation
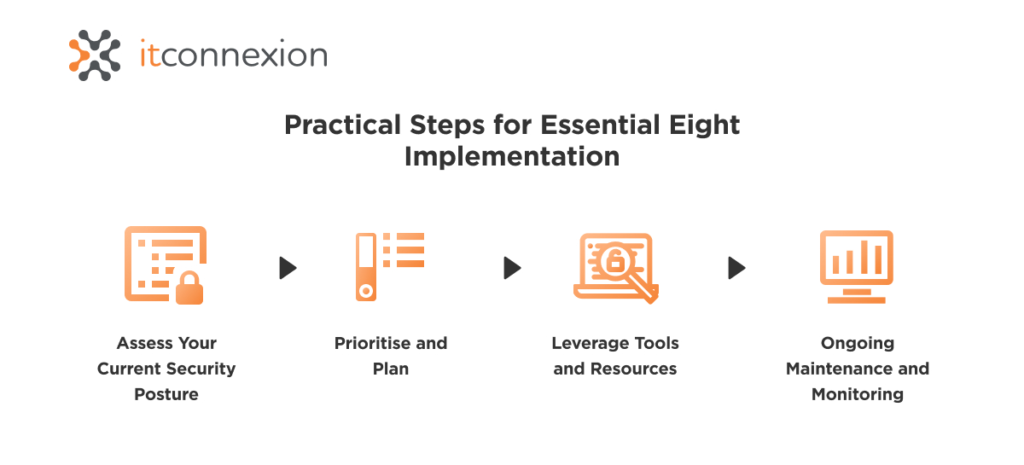
- Assess Your Current Security Posture:
Conduct a thorough assessment to identify existing gaps and areas for improvement.
- Prioritise and Plan: Develop a prioritised action plan based on the identified gaps and the criticality of the systems involved.
- Leverage Tools and Resources:
Utilise cybersecurity tools and services to assist with the implementation and management of the Essential Eight strategies.
- Ongoing Maintenance and Monitoring:
Regularly review and update your cybersecurity measures to ensure they remain effective against emerging threats.
Case Studies and Success Stories
Implementing the Essential Eight has proven to be effective for many organisations. For instance, a midsize business that adopted these strategies reported a significant reduction in security incidents and improved overall system resilience. Another nonprofit organisation found that by following the Essential Eight guidelines, they were able to meet compliance requirements more easily and protect their sensitive data more effectively.
Conclusion
Adopting the Essential Eight Cybersecurity framework is a crucial step in protecting your business from cyber threats. By implementing these strategies, you can enhance your security posture, comply with industry standards, and reduce the risk of cyber incidents.
At ITConnexion, we specialise in helping businesses like yours navigate the complexities of cybersecurity. Our team of experts is ready to assist you in implementing the Essential Eight and strengthening your defenses.
Contact us today to learn more about how we can support your cybersecurity needs and ensure your business remains secure in the digital age.





