
Essential Eight Cyber Security
Discover Your Essential Eight Posture & The Best Strategy for Your Organisation
What is The Essential Eight
Essential Eight is a set of cyber security mitigation strategies developed by the Australian Cyber Security Centre (ACSC). Recommended by the Australian Government, these strategies are designed to significantly reduce cyber security risks and make it harder to compromise systems. By implementing the Essential Eight framework, organisations can strengthen their cyber security posture through targeted actions.
Strategies to Mitigate Cyber Security
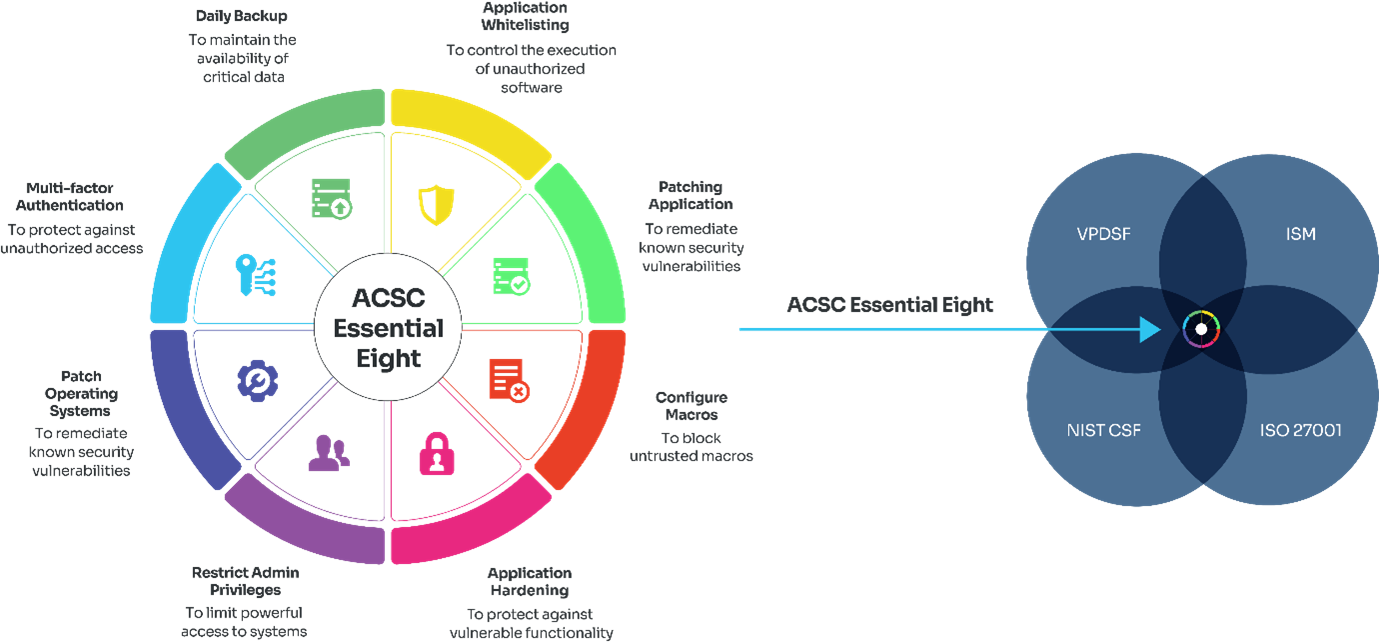
ACSC Essential Eight
Who Should Implement the Essential Eight?
Every organisation that values the security of its data and operations must safeguard its systems against cyber threats.
Here’s a closer look at who should prioritise the implementation of the Essential Eight:
- Small to Medium Enterprises (SMEs):
SMEs are often targets for cyber attacks due to their typically lower levels of security compared to larger enterprises. Implementing the Essential Eight can significantly bolster their defenses, ensuring business continuity and protecting sensitive customer and business data.
- Not-For-Profit Organisations (NFPs):
NFPs handle a variety of sensitive information, from donor details to operational data. Protecting this information is vital not only for the organisation’s reputation but also for maintaining trust with stakeholders. The Essential Eight provides a robust framework to secure their digital assets.
- Government Agencies:
Government entities are prime targets for cyber attacks due to the sensitive nature of the data they handle. The Essential Eight is particularly relevant for these agencies as it aligns with national cyber security standards and practices, ensuring compliance and enhanced security.
- Financial Institutions:
Banks, credit unions, and other financial institutions manage highly sensitive financial data. Implementing the Essential Eight helps in fortifying their cyber security measures against threats, ensuring the protection of financial transactions and personal customer information.
- Healthcare Providers:
Healthcare organisations store and process vast amounts of personal health information (PHI). The Essential Eight helps safeguard this data against breaches, ensuring compliance with health data regulations and maintaining patient confidentiality.
- Educational Institutions:
Schools, colleges, and universities manage a wide range of data, from personal student information to research data. Implementing the Essential Eight helps these institutions protect their networks from cyber threats, safeguarding their intellectual property and personal data.
- Legal Firms:
Legal professionals handle sensitive client information and case data. By adopting the Essential Eight, law firms can protect this information from unauthorised access and cyber threats, ensuring client confidentiality and data integrity.
- Retail and E-commerce Businesses:
These businesses handle a significant amount of customer data, including payment information. Implementing the Essential Eight helps protect this data from cyber threats, ensuring customer trust and compliance with data protection regulations.
Why The Essential Eight Matters
Implementing the Essential Eight is not just about compliance; it’s about proactively protecting your organisation from the ever-evolving landscape of cyber threats. By adopting these strategies, you are taking a significant step towards ensuring the safety and security of your organisation’s digital assets.
Contact Our Cyber Security Experts to Discuss Your Organisation's Best Strategy
The Mitigation Strategies of Essential Eight
- Application Whitelisting
- Patching Application
- Configuration of Microsoft Office Macro Settings
- User Application Hardening
- Restricting Admin Privileges
- Operating System Patching
- Multi-Factor Authentications
- Daily Backups
By implementing the Essential Eight, the organisation will be more cost-effective in terms of time, money, and effort than having to respond to a large-scale cyber security incident.
Application Control:
- Work with management to prepare an approved list of applications for staff to use
- Implement application whitelisting to allow only approved applications to run
- Regularly review and update the list of allowed applications
Patch Applications:
- Regularly scan for application updates
- Keep software applications (such as browsers, PDF readers, etc.) up to date with the latest security patches
- Prioritise critical vulnerabilities and apply patches promptly
- Regularly update operating systems (OS) with security patches
- Focus on critical vulnerabilities affecting the OS
Patching System Operations:
- Regularly update operating systems (OS) with security patches
- Focus on critical vulnerabilities affecting the OS
- Devices no longer receiving security updates are replaced
Configure Microsoft Office Macro Settings:
- Disable macros by default in Microsoft Office applications
- Prevent users from being able to enable macros without authorisation
- Enable macros only for trusted documents and users
User Application Hardening:
- Implement optimised security settings for commonly used programs (e.g. Chrome, Edge, Adobe, etc.)
- Prevent users from being able to modify settings or install extensions/add-ons without approval
- Educate users about safe practices when using applications
- Encourage them to avoid risky behaviours (e.g., clicking on suspicious links, downloading unknown files)
Restrict Administrative Privileges:
- Limit administrative access to authorised personnel
- Block privileged accounts from web and email access
- Use separate accounts for administrative tasks
Multi-factor Authentication (MFA):
- Require users to provide an additional authentication factor (e.g., SMS code, app notification) along with their password
- Enable MFA for critical systems and accounts
Daily Backups:
- Regularly back up critical data and systems
- Test backup restoration procedures periodically
You can contact us for further information on Essential Eight Mitigation Strategies
Different Maturity Levels in The Essential Eight
4 different maturity levels have been identified (Maturity Level 0 through to Maturity Level 3). Apart from Maturity Level 0, all the maturity levels are based on mitigating increasing levels of adversary tradecraft (e.g., tactics, techniques, tools, and procedures).
Organisations need to consider the chance of being targeted for cyber security incidents and it will depend on the security measures that have been taken for the safety of their system and data to keep them secure. With the combinations of each maturity level applied through the Essential Eight baseline, they can be used to help determine which level the organisation’s at and which element needs to be implemented.
Maturity Level 0
Indicates that an organisation is lacking critical security elements, or is not actively making efforts to defend itself from attacks
Maturity Level 1
Indicates that the organisation’s cyber security posture should be able to defeat the most common attacks, generally able to defeat low-effort attacks. This maturity level is suitable for most Australian organisations that do not have significant data security or financial protection requirements.
Maturity Level 2
Indicates that your organisation’s cyber security position should be able to deal with attackers who invest more time in targeted attacks and use more effective tools. This maturity level might be the best solution for mid-size organisations with one or more critical systems.
Maturity Level 3
Indicates that your organisation can manage more adaptive cyber attackers that are less dependent on public tools and techniques and spend more time and effort to overcome the target’s implemented security controls.
What Maturity Level Should be a Good Target for an Organisation?
In general, Maturity Level 1 will be a good start for small to medium enterprises. Maturity Level Two can be suitable for large enterprises and Maturity Level Three may be suitable for critical infrastructure providers & other organisations that operate in high threat environments.
Steps to Implement the Essential Eight
Understand the Importance
Start by familiarising yourself with the Essential Eight, a set of cyber security strategies provided by the Australian Cyber Security Centre. These are crucial for protecting your organisation against cyber threats. You can download the Essential Eight Guide for free here.
Assess Your Current Practices
Take a short assessment provided by ITConnexion to evaluate your current cyber security measures. The assessment will ask questions about how you manage cyber security for your business and determine your current cyber security maturity level. Based on your answers, you will receive guidance on areas for improvement.
Consult with Our Experts
Schedule a short meeting with our cyber security team to discuss the results of your assessment and identify specific areas for enhancement in your current practices.
Enhance Your Cyber Security
Implement the recommended improvements to your cyber security measures and determine the resources and assistance required to fully adopt the Essential Eight.
To get started, take our self-assessment and begin enhancing your cyber security with ITConnexion!
