Organisations are recommended by the Australian government to implement eight essential mitigation strategies from the Australian Cyber Security Centre (ACSC)’s Strategies to Mitigate Cyber Security Incidents as a baseline. This baseline, known as the Essential Eight, makes it much harder for adversaries to compromise systems.
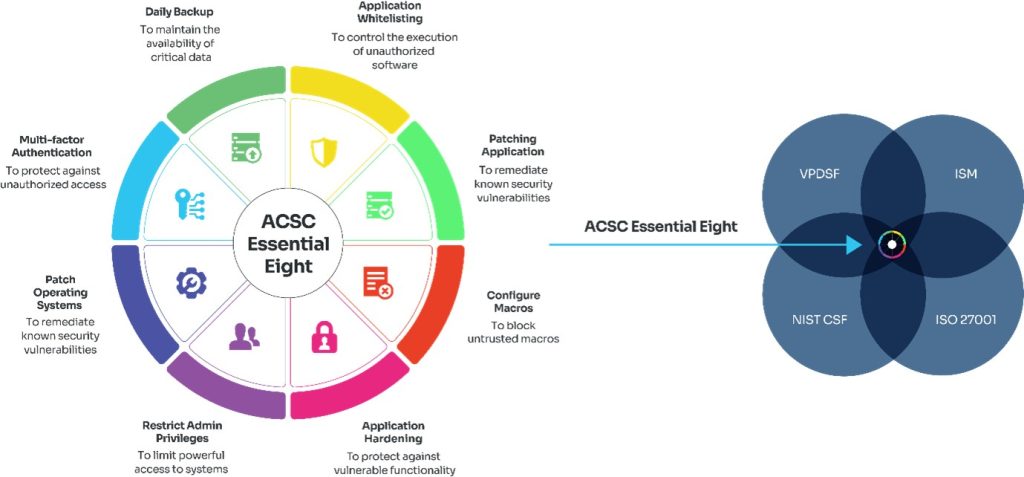
The mitigation strategies of Essential 8 include: Application Whitelisting, Patching Application, Configuration of Microsoft Office Macro Settings, User Application Hardening, Restricting Admin Privileges, Operating System Patching, Multi-Factor Authentications, and Daily Backups.
By implementing the Essential 8, the organisation will be more cost-effective in terms of time, money, and effort than having to respond to a large-scale cyber security incident.
Different Maturity Levels in The Essential 8
4 different maturity levels have been identified (Maturity Level Zero through to Maturity Level Three). Apart from Maturity Level Zero, all the maturity levels are based on mitigating increasing levels of adversary tradecraft (e.g., tactics, techniques, tools, and procedures).
Organisations need to consider the chance of being targeted for cyber security incidents and it will depend on the security measures that have been taken for the safety of their system and data to keep them secure. With the combinations of each maturity level applied through the Essential 8 baseline, they can be used to help determine which level the organisation’s at and which element needs to be implemented.
- Maturity Level 0: Indicates that an organisation is lacking critical security elements, or is not actively making efforts to defend itself from attacks
- Maturity Level 1: Indicates that the organisation’s cybersecurity posture should be able to defeat the most common attacks, generally able to defeat low-effort attacks. This maturity level is suitable for most Australian organisations that do not have significant data security or financial protection requirements.
- Maturity Level 2: Indicates that your organisation’s cybersecurity position should be able to deal with attackers who invest more time in targeted attacks and use more effective tools. This maturity level might be the best solution for mid-size organisations with one or more critical systems.
- Maturity Level 3: Indicates that your organisation can manage more adaptive cyber attackers that are less dependent on public tools and techniques and spend more time and effort to overcome the target’s implemented security controls.
Click here for more detailed information on the Essential 8 Maturity Model and Maturity Levels.
How to Implement Mitigation Strategies as a Package?
Organisations that have implemented each of the elements from the Essential 8 strategies individually will result in their maturity level rating being determined.
With previous cyber security measure approaches, it was seen as leading to an imbalanced cyber security posture as some mitigation strategies were not addressed or addressed at a lower maturity level.
If an organisation can achieve a higher maturity level rating as a package, this will result in a more broad coverage of various cyber security threats.
All organisations are recommended to achieve a consistent maturity level across all 8 mitigation strategies before stepping into a higher maturity level.
What Maturity Level Should be a Good Target for an Organisation?
In general, Maturity Level One will be a good start for small to medium enterprises. Maturity Level Two can be suitable for large enterprises and Maturity Level Three may be suitable for critical infrastructure providers & other organisations that operate in high threat environments.
Make an appointment today for the Essential 8 Assessment:
- The importance of the Essential 8 for the organisation
- To identify the cyber security strengths of the organisation
- To understand areas where the business can improve
- To know how to improve your cyber security measures and where to find help
The assessment will ask you questions about how you manage cyber security for your business. Based on your answers, it will determine your current cyber security maturity level. It will then provide you with guidance on how to improve.





